Mastering Linux File Permissions and Access Control Lists
Day - 6 of 90daysofDevOps
The legacy of the Linux commands
Following from the Day - 5 streaks of learning Linux commands and shell scripting, there is something really simple yet a must-have tool for any Linux user or administrator. The man command in the Linux operating system stands for "manual," and it is used to view the system's online reference manual pages. These manual pages explain in detail the numerous commands, system calls, library functions, and configuration files that are available on your Linux system. The man command is an essential tool for both new and seasoned users to quickly learn the functions and usage of various commands and utilities.
Let's quickly consult Ryan (our IT admin from the previous post) to understand the usage of this command:

The syntax for the man command is pretty simple:
man [section_number] <command name>
While the section number is an optional component in the syntax, you can just write man <command name> as shown below

So, tell me, what does this do? man displays the manual for the command that we have asked for, outlining how to use it and what features are available.

If you look at the bottom of the highlighted screenshot, it asks if we want additional help; you can use 'h' for help, or if you discovered what you were looking for, you can exit the manual by pressing the 'q' button. A very handy and valuable tool in any Linux user's or administrator's toolset!!
The File and Folder Permissions
After you've learned how to use the "man" command, I'd want to go over a separate but highly helpful idea called File Permissions and Access Lists. This function is essentially an identity and access management capability or a wonderful security solution for the files we work with under Linux.

Hmmm... great to see these 3. But how do these three work with file permissions?
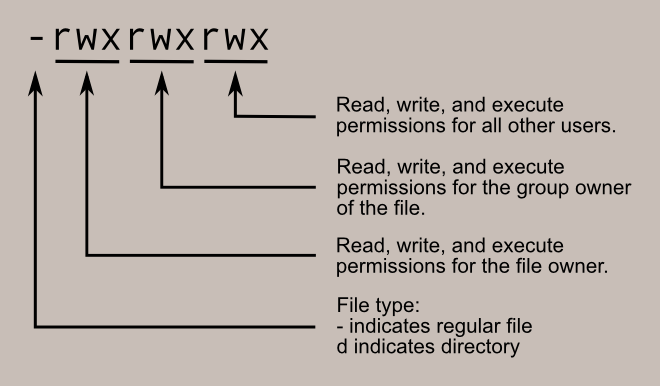
While the file owner, group owner, and other users will all have 3*3 file rights, the very first bit of the permission determines whether this is a file or a directory. If the first bit is 'd,' it means that the object we're looking at has directory rights; otherwise, it's a file.
Take a look at the below screenshot where there is a text file called "firstfile.txt" and there is a default directory ".ssh"


PS: The screenshot was taken after the completion of this activity. Hence the file permissions are all modified.
Alright! That gave us an idea of what can be the permissions and how we identify if the object we are looking at is a file or a directory. What next?
Let's run the "ls -al" command to see the permissions for the files and folders in the current working directory and look at the text file we have created.


When I spoke to Ryan, I was determined to understand how I can set a read-only permission on the firstfile.txt
Indeed, he was kind and told me to run the chmod command with the first set enabled since I was the owner and I just needed the file to be read-only.
Chmod Calculator can be of great help if you are new to calculating permissions.
Once I made my calculations and ran the chmod command, I wanted to verify if that command set the right permissions for the file. So I ran the ls -al command again and booooommmm!!! I was able to change the permissions.

Since the file was read-only I wanted to double-check if i actually understood what Ryan had gracefully taught me. So i tried changing the permissions now to read-write-execute for the file owner. That went well too!!!

Alright!! Now that we have all understood about the file permissions, it's time to understand two great commands from access control.
Access Control Lists
getfacl
In Linux, the getfacl tool displays the Access Control Lists (ACLs) of files and directories. ACLs go beyond the standard owner, group, and other permissions to provide a more granular mechanism to restrict access permissions. The getfacl command displays the additional permissions assigned to specified users and groups for a given file or directory.
Syntax: getfacl [options] [file/directory]
Let's talk with an example and use our newly created firstfile for the exercise.

The getfacl command returned me the name of the file, the owner, and the group as well. Along with these attributes, the command also displays the permissions respectively.
I am pretty sure you have the next question for me... Alright, what if I want to set the access control list? That's our next instruction.
setfacl
In Linux, the setfacl command is used to configure Access Control Lists (ACLs) for files and directories. ACLs go beyond the typical owner, group, and others rights to provide a more fine-grained method of managing access permissions. Individual users and groups can be granted specified permissions on a file or directory using setfacl.
Syntax: setfacl [options] acl_spec file/directory
Let's work out the setfacl command with the same firstfile and see how that works.
To understand the setting up of access control list for the current user which is ec2-user since this is linux on AWS, I will provide the access to the same user. Let's get that working on the terminal and look at what changes in the permissions.

With the setfacl command now properly executed without issues and also the permissions re-written, it is now time for us to see if the ACL for that file changed. So we know what's next on pipeline for us. Yes!!! you got that correct.. Run the getfacl command.

That's amazing!! isn't it? Glad that there are so many ways to secure our files and access controls. Let me hand you a bonus tip... while ls -al gives me all the file permissions for all the files and folders, there is a "-ltr" switch that works great with ls command. This switch is a useful way to view files and directories, especially when you want to see the most recently modified ones at the bottom.
Here's a breakdown of the options used in the ls -ltr command:
l: Displays the output in long format, providing detailed information about each file and directory. The long format includes file permissions, number of links, owner, group, file size, modification date, and filename.t: Sorts the output based on the modification time (timestamp) of the files and directories. The most recently modified files appear at the bottom of the list.r: Reverses the order of the sorting, so the oldest files appear at the top and the most recently modified files appear at the bottom.


Conclusion
Security of files and folders is a crucial part of the infrastructure. Especially when it is all about data security, these are lethal tools that can safeguard you as a first line of defense. Hopefully, I was able to convey how critical these are!
Happy Learning!
